Looking Ahead: From the Classic VPN to the Unified Network Control Point (2GC CloudBridge)
Transition from VPN gateways to UNCP: modern QUIC/HTTP-3 protocols, Zero Trust architecture, and unified network control in 2GC CloudBridge.
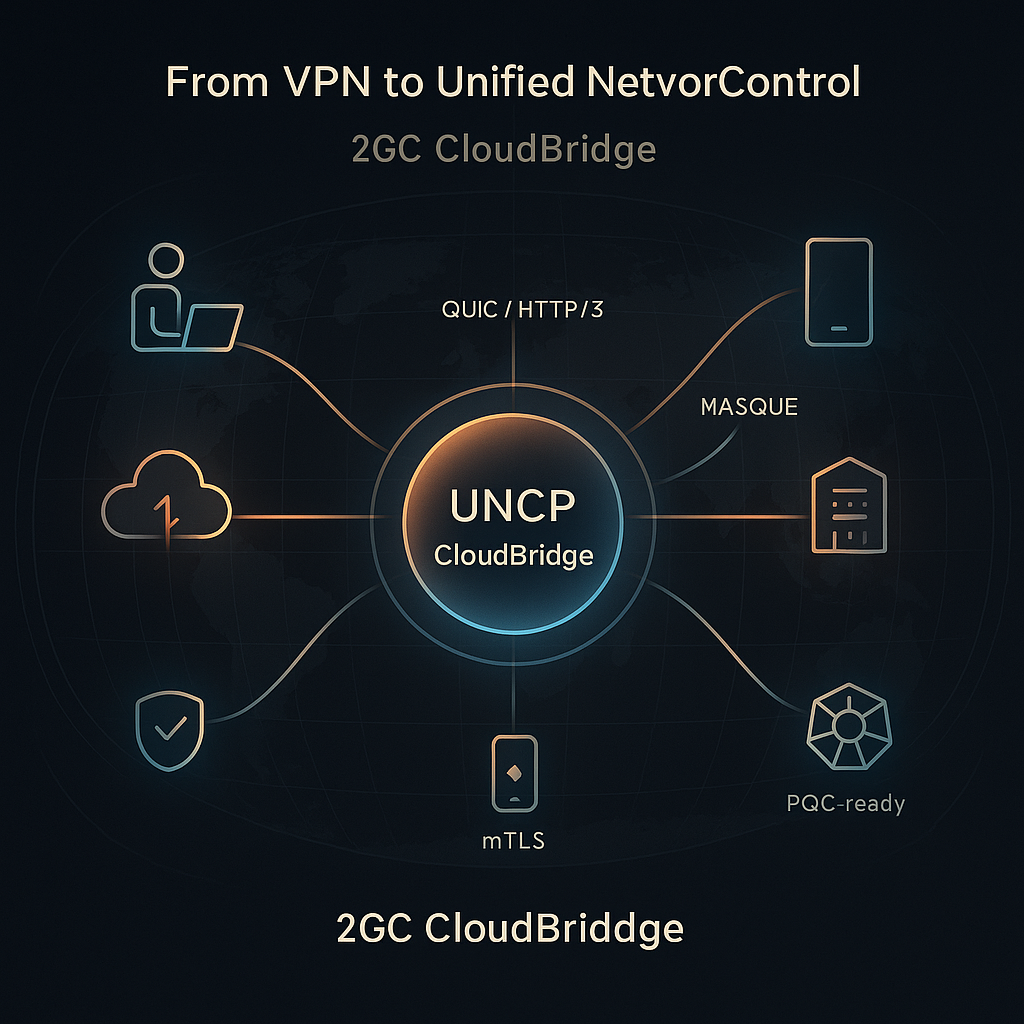
Looking Ahead: From the Classic VPN to the Unified Network Control Point (2GC CloudBridge)
For two decades, “secure corporate connectivity” almost reflexively meant “deploy a VPN gateway and hairpin everyone through it.” That perimeter mindset no longer matches the Internet we actually run on. The transport layer is moving to QUIC and HTTP/3, tunneling is being reimagined inside modern web protocols, and Zero Trust has become an architectural baseline rather than an aspirational slogan. At the same time, European regulations like DORA and NIS2 are turning operational resilience, logging, and third-party risk into legal obligations rather than best practices. In this new environment, enterprises are replacing box-centric VPN architectures with Unified Network Control Points—cloud-first platforms that fuse transport, identity, and policy into a single control plane.
What a Unified Network Control Point Actually Is
A UNCP is not just “another tunnel.” It’s an architectural pattern that centralizes three planes of control. The data plane uses contemporary transports—HTTP/3 over QUIC and standardized proxying—so private traffic rides on the same resilient rails as today’s web. The trust plane embeds Zero Trust policy so access is decided per user, per device, and per resource rather than by IP reachability. And the compliance plane consolidates telemetry, incident handling, and supplier oversight to meet fast-tightening regulatory requirements. Taken together, this replaces the brittle perimeter implied by a single VPN appliance with a service that is closer to how modern applications are built and consumed.
Why the Internet’s Direction Favors “VPN-less” Access
The transport of the web has been quietly but decisively upgraded. QUIC (RFC 9000) delivers 0-RTT connection setup, stream multiplexing without head-of-line blocking, and seamless path migration; HTTP/3 maps web semantics onto that transport. On top of those foundations, the IETF’s MASQUE work standardized proxying of both UDP (CONNECT-UDP, RFC 9298) and arbitrary IP packets (CONNECT-IP, RFC 9484), turning “a VPN through HTTPS” from a hack into a first-class, standard protocol family. That is the technical basis for resilient, middlebox-friendly private connectivity without falling back to legacy, box-terminated IPsec overlays.
Crucially, this is not theoretical. Apple’s iCloud Private Relay and large consumer/privacy services already use dual-relay designs powered by QUIC/MASQUE, proving the model at massive scale. When Relay is enabled, traffic is split across two independent relays so no single party sees both who you are and where you go—an illustrative pattern for enterprise control planes that want stronger privacy guarantees by construction.
Adoption data confirms the trend: by August 2025, HTTP/3 is used by roughly 35% of all websites (and closer to 40% among the top one million), a year-over-year rise consistent with Cloudflare Radar’s broader view of HTTP/3 growth across the Internet. The web’s “physics” have changed; private connectivity should align with it.
Privacy enhancements are evolving alongside transport. Oblivious HTTP (RFC 9458) introduces a standardized double-proxy pattern for forwarding encrypted HTTP messages such that the origin cannot link requests to the same user. For enterprises orchestrating multi-tenant relays, OHTTP is a useful building block for minimizing metadata exposure in control and telemetry paths.
The Trust Plane: Zero Trust and Device Attestation
Zero Trust, as described in NIST SP 800-207, moves defenses from static, network-based perimeters toward per-request decisions bound to users, assets, and resources. In practice, that means identity-aware, app-level access instead of flat network reachability. For high-assurance scenarios, IETF RATS (RFC 9334) adds remote attestation—verifying the device’s integrity before granting access—closing one of the biggest blind spots in classic VPN models where a compromised endpoint can bring the “inside” with it.
The Compliance Plane: DORA and NIS2 as Architectural Drivers
The regulatory backdrop now explicitly favors centralized control and observability. The Digital Operational Resilience Act (DORA) has applied since January 17, 2025, and it compels EU financial entities to evidence ICT resilience, report incidents, and govern critical ICT third parties. Meanwhile, the NIS2 Directive extends security and reporting duties across a wide range of sectors, with transposition deadlines in late 2024 and fresh ENISA guidance in 2025. A UNCP—where access, logs, workflows, and supplier integrations concentrate—simplifies demonstrating continuous control to supervisors.
Security Reality Check: Edge VPN Appliances as Risk Concentrators
Recent incidents have underscored the systemic risk of relying on perimeter VPN boxes as “the one door in.” In early 2024, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued Emergency Directive 24-01 addressing active exploitation of Ivanti gateway vulnerabilities—mandating aggressive mitigation steps across federal agencies. Beyond the specifics of any one vendor, the episode illustrates a structural weakness: when a single edge appliance is both the entry point and trust anchor, its compromise has outsized blast radius. Shifting control into cloud-managed, identity-centric planes reduces that concentration of risk.
Where 2GC CloudBridge Fits
2GC CloudBridge embodies the UNCP pattern. On the data plane, it speaks the languages the modern Internet favors—TLS 1.3, HTTP/3/QUIC, and WireGuard—supporting both client-to-service and service-to-service topologies, including P2P mesh where edge or IoT deployments benefit from locality. On the trust plane, it externalizes identity and policy through Keycloak (SSO, RBAC, token-based access), and its design is open to integrating remote attestation for device posture before any route or token is issued. On the compliance plane, CloudBridge couples rich observability (Prometheus, Grafana, Jaeger, Loki) with Cadence-driven workflows that automate “Day-2” operations—incident response, backup/restore drills, access reviews, and audit trails aligned to DORA/NIS2 reporting needs. The result is not “a better VPN,” but a control point that speaks in applications and identities rather than subnets and ports—matching how enterprises actually work today.
Cryptography for the Next Decade: Be Crypto-Agile, Go Post-Quantum
Transport encryption by default is table stakes. The strategic differentiator now is crypto-agility—designing the control and data planes so key exchange, signatures, and PKI can transition without downtime. Here the standards are clear: in August 2024 NIST finalized the first three post-quantum cryptography FIPS standards—FIPS 203 (ML-KEM) for key establishment and FIPS 204 (ML-DSA) plus FIPS 205 (SLH-DSA) for digital signatures. Planning CloudBridge deployments so they can introduce ML-KEM handshakes and ML-DSA/SLH-DSA signatures in a phased manner protects today’s data against tomorrow’s adversaries—and against “harvest-now, decrypt-later” risks.
Market Direction: Convergence and Consumption
Industry signals point the same way. SASE/SSE platforms that unify networking and security are gaining share, and independent analysts forecast steady growth and a tilt toward single-vendor platforms as enterprises prioritize simplicity and integrated policy. In parallel, Network-as-a-Service (NaaS) models are expanding, replacing capital-intensive device fleets with subscription consumption of connectivity and controls. A UNCP like CloudBridge can be the connective tissue: the single place where identity, transport, and telemetry meet, regardless of the underlying access mix.
How to Get There Without the Drama
The transition away from a box-centric VPN does not require a “big bang.” Most organizations start by moving from network-level exposure to application-level access with SSO and per-resource policy—letting users reach “the CRM” or “the admin console” rather than a whole subnet. The transport then shifts to HTTP/3/QUIC with standardized MASQUE tunneling so mobile clients and branch sites ride a path that survives NATs and captive networks gracefully. Device posture checks grow into attestation for the most sensitive roles. Telemetry and workflows in the UNCP become the anchor for incident reporting, tabletop exercises, and supplier oversight under DORA/NIS2. Over time, the old VPN recedes from the critical path, kept only as a compatibility escape hatch for a few legacy systems.
The Bottom Line
Classic corporate VPN servers were the right tool for a different Internet. The Internet we have now runs on QUIC and HTTP/3, supports standard, stealthy proxying of UDP and IP, and expects Zero Trust at the point of decision. Regulations demand centralized evidence of control, and the risk model punishes single edge boxes. In that world, Unified Network Control Points—2GC CloudBridge foremost among them—are not a trend but a logical consequence: a smaller attack surface, application-centric access, richer visibility, and an operational model that evolves with the network itself.
Selected References
- Transport & tunneling: QUIC (RFC 9000) and HTTP/3 (RFC 9114); MASQUE proxying for UDP (RFC 9298) and IP (RFC 9484)
- Privacy relay patterns: Apple’s iCloud Private Relay (dual-relay architecture using modern standards)
- Adoption data: W3Techs HTTP/3 usage (Aug 2025); Cloudflare Radar 2024 Year-in-Review
- Zero Trust & attestation: NIST SP 800-207; IETF RATS (RFC 9334)
- Regulation: DORA application since Jan 17, 2025 (ESMA/EIOPA); NIS2 overview and ENISA implementation guidance (2025)
- Risk of VPN edge appliances: CISA ED 24-01 on Ivanti gateways (2024)
- Post-quantum standards: NIST FIPS 203/204/205 finalized (Aug 2024)
- Market direction: Dell’Oro Group on SASE growth; NaaS market trajectories (Fortune Business Insights)